Security – Pass hash attack for Yahoo Messenger
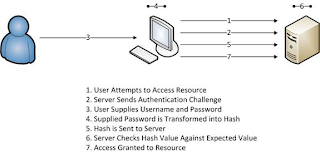
Authentication is an important process of a internet service for authenticating users. For example, when you register an account for Yahoo mail, you will be asked for an ID and password so that only you can access to your email account. That means Yahoo will save your ID and your password in their servers so that they can compare with your input later. Your ID can be saved in clear text but the password will not be never saved under clear text. Yahoo uses its own algorithmus to make a hash of your password. For example your password is "123456789″, then Yahoo may save it as format "25f9e794323b453885f5181f1b624d0b". In this way only you know the password and if the server is attacked, your password will be still safe. Furthermore password hash protects you from losing password through snipping on network connection.A normal authentication looks like below
Now, let's consider a scenario. What if I manually establish a connection to the email I would like to access, but rather than feeding it privileged username and password I feed it the username and that password hash that I have stolen? Yahoo is concerned about is receiving a hash that matches what it is expecting (password hash). This means that I don't have to perform the one-way hashing function on the password, I just have to supply the hash, which is the basis for this attack. We call this attack "password hash attack" and the authentication will look like image below
So end with theorie and start with a small pratice of "password hash attack" with Yahoo Messenger. If you use Yahoo Messenger, there is an option to save your ID and password.
This password again is of course not saved under clear text but its hash will be saved in registry and sent to server for authentication when user logs in Yahoo Messenger. Therefore we can make a password hack attack for Yahoo Messenger as following steps.
0. Somehow take an access to the computer of victim. Open Yahoo Messenger and see if the option of saving ID and Password is ON. If it's on, we can start our attack.
1. Press Windows + R. Type in "regedit". Enter.
2. Browse to "HKEY_CURRENT_USER\Software\Yahoo\Pager".
3. Right click on it and click "Export". Enter a file name to save registry information into .reg file.
4. Copy the .reg file from victim's computer to our computer. Open it with Notepad, delete all of values but
+ "Save Password"
+ "MD_ID_VALUE"
+ "Yahoo! User ID"
+ "ETS"
5. Double click to import this .reg file into our registry.
6. Open your Yahoo Messenger and click Log In. Suprise you are logging to account of victim.
Với phiên bản 10.0.0.1264 thì không có MD_ID_VALUE, và không cần MD_ID_VALUE thì vẫn được.





Không có nhận xét nào:
Đăng nhận xét